Nutanix Flow Network Security
Multicloud Security for Apps and Data

Nutanix Flow Network Security
Contact us for Pricing!
Start a Chat
Security is complex, but protecting critical assets shouldn't be. Flow Network Security creates software-based firewalls for your critical apps and data without the management overhead.
Overview:
The network is the foundation for the connected Enterprise. With increasing application complexity, driven by distributed services and rapid growth in SaaS and cloud-based offerings, the need to easily visualize, analyze and govern network communications becomes critical.
Nutanix Flow delivers advanced network security, providing visibility into the virtual network, application-centric protection from network threats, malware, and ransomware and security and compliance monitoring.
Flow allows organizations to deploy software-defined virtual network security without the complexity of installing and managing additional products that have separate management and independent software maintenance requirements.
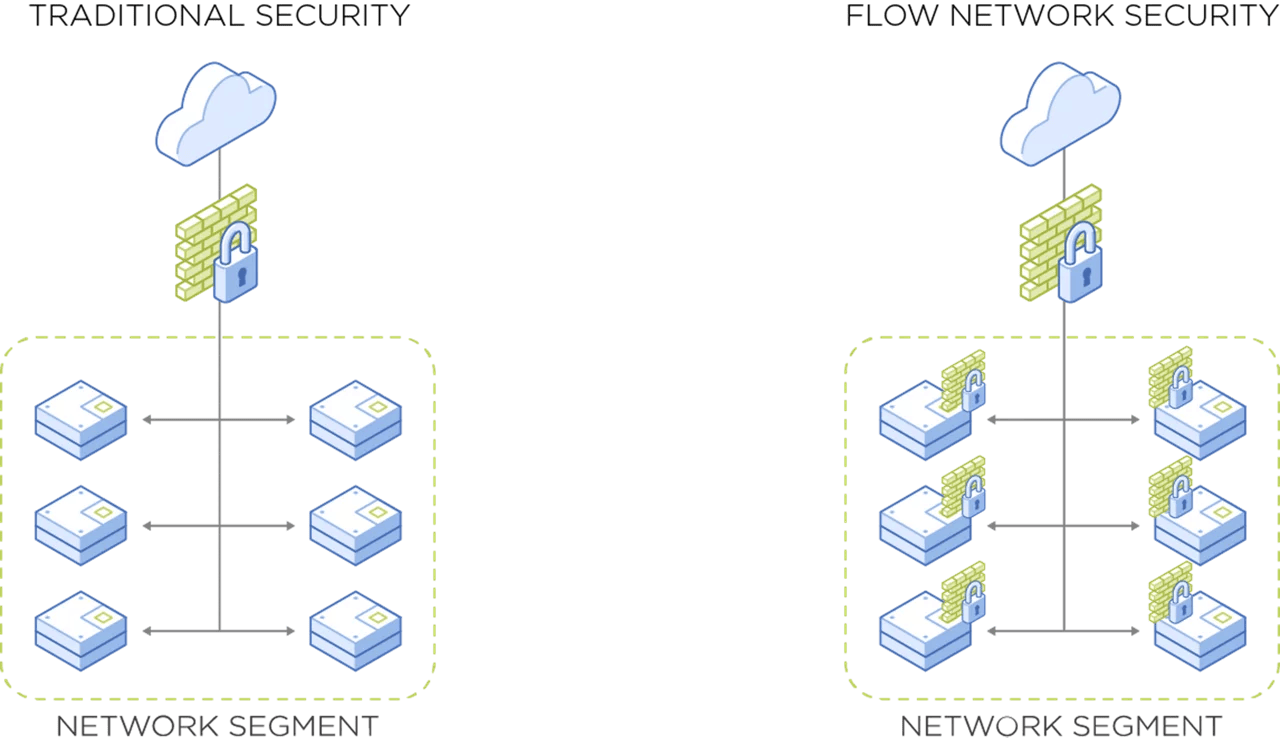
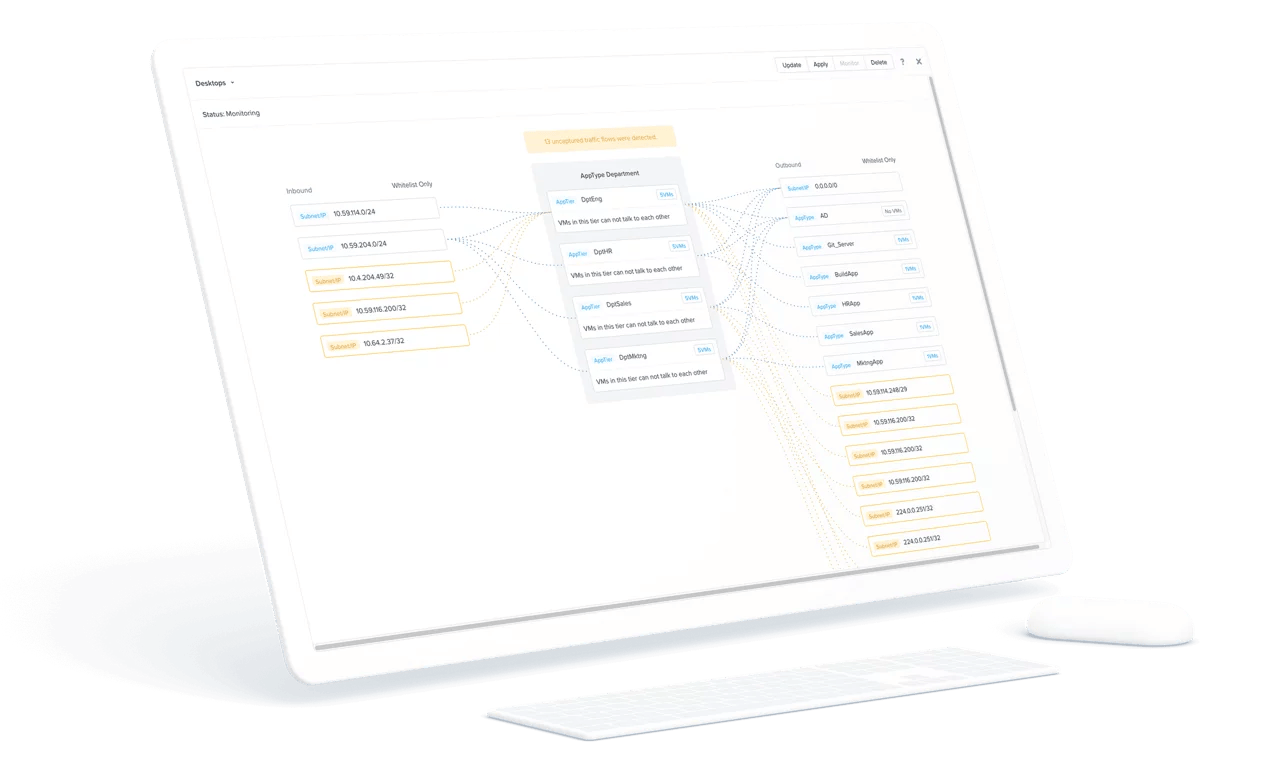
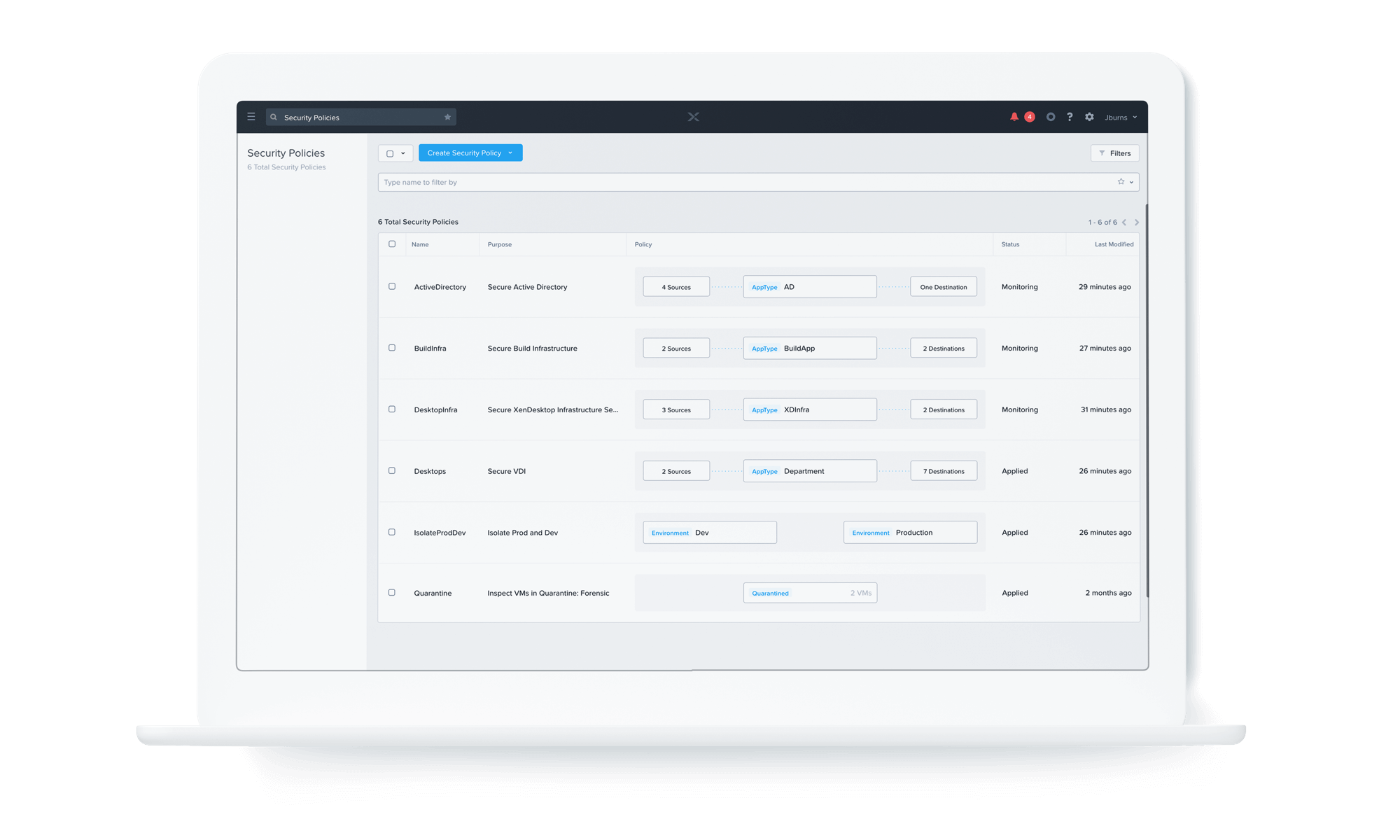
Fully integrated into the Nutanix private cloud solution and Nutanix AHV virtualization, Nutanix Flow differs from traditional perimeter firewalls by allowing network policy to be attached to VMs and applications, rather than specific network segments (e.g., VLANS) or identifiers (IP addresses). Through centralized management from Prism, policies are auto-updated throughout the VM lifecycle, removing the burdens of change management.
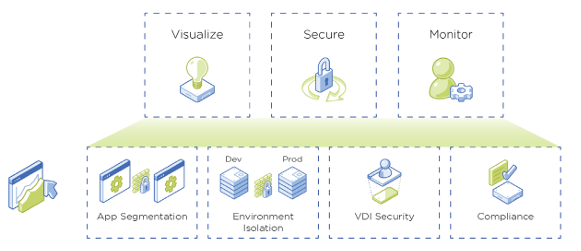
Functions
- VM Microsegmentation
- Application Visualization
- Service Chaining
- Policy-based Control
- Identity Based Policy
- Traffic Monitoring and Threat Detection
- Compliance Audit and Reporting
Key Benefits
- Application centric network policies for VMs
- Works with any network topology or architecture
- Application and network visibility
- Policy change management tied to VM lifecycle
- Prevent the propagation of network security threats
- Adds Identity based security to EUC/VDI deployments
- Security posture visibility and tracking dashboard
- Compliance audit and reporting regulations like HIPAA, PCI, NIST, and more
- Expand functionality via thirdparty network inspection and policy tools